Business Email Compromise Best Practices
Obwohl es zahlreiche Arten gibt gibt es im Wesentlichen zwei Hauptmechanismen ber die Angreifer mit BEC-Techniken in Unternehmen eindringen. Although there are numerous types there are essentially two main mechanisms through which attackers penetrate organizations utilizing BEC techniques spoofing and account take-over attacks.

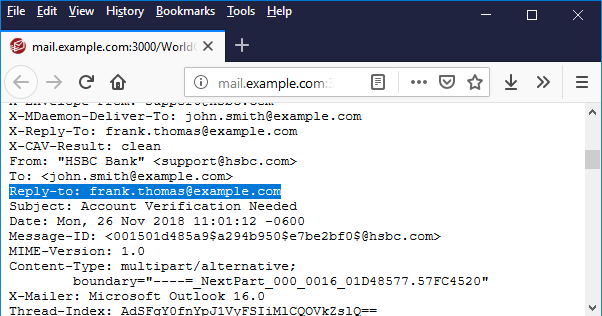
How To Tell If An Email Is Fake Or Real
Business email compromise BEC is an ever-present and growing threat to organizations of all sizes.
Business email compromise best practices. OPS Business Email Compromise Guide Documents A guide providing best practices on what to do to safeguard the email system of a business from being compromised. Although there are numerous types there are essentially two main mechanisms through which attackers penetrate organizations utilizing BEC techniques spoofing and account take-over attacks. In the FBIs recently released Internet Crime Report IC3 for 2018 BEC caused the greatest dollar losses of all reported internet crimesTotal losses from BEC have more than doubled since 2017 to over 12 billion or about 63000 per incident.
By rootdaemon July 29 2021. Best Practices to Thwart Business Email Compromise BEC Attacks. Although there are numerous types there are essentially two main mechanisms through which attackers penetrate organizations utilizing BEC techniques spoofing and account take-over attacks.
In a recent study 71 of organizations acknowledged they had seen a business email compromise. Use this collection of tips and best practices to help strengthen your organizations defenses against one of the most pervasive methods of fraud. Business email compromise BEC refers to all types of email attacks that do not have payloads.
As essential as email is too many of us do it poorly. Business email compromise BEC refers to all types of email attacks that do not have payloads. SunTrust Advantage Products Services.
Business email compromise BEC is one of the most financially damaging online crimes. Although there are numerous types there are essentially two main mechanisms through which attackers penetrate organizations utilizing BEC techniques spoofing and account take-over attacks. Obwohl es zahlreiche Arten gibt gibt es im Wesentlichen zwei Hauptmechanismen ber die Angreifer mit BEC-Techniken in Unternehmen eindringen.
Best Practices to Thwart Business Email Compromise BEC Attacks Posted by The Hacker News at July 29 2021. To pull one off cyber criminals have to dig deep into your company records to understand your purchasing habits and the personnel who handle financial transactions then gain access to a specific persons account in order to deceive another employee. Business email compromise BEC refers to all types of email attacks that do not have payloads.
Although there are numerous types there are essentially two main mechanisms through which attackers penetrate organizations utilizing BEC techniques spoofing and account take-over attacks. After informally surveying some successful and effective people Ive compiled a list of best practices for the current business environment. Der Begriff Business Email Compromise BEC bezieht sich auf alle Arten von E-Mail-Angriffen die keine Nutzdaten enthalten.
Business Email Compromise BEC is one of the most pervasive cyber threats facing enterprises. In a recent. Corporate Commercial MENU.
Fraudsters by impersonating executives partners and vendors will try to trick your employees. Business email compromise BEC refers to all types of email attacks that do not have payloads. Investing Retirement MENU.
Der Begriff Business Email Compromise BEC bezieht sich auf alle Arten von E-Mail-Angriffen die keine Nutzdaten enthalten. Your Priorities Our Approach Solutions and Tools Specialty Groups Find an Advisor View Main Menu. Business Email Compromise email using lookalike domain Compromised Email Account Another common tactic is the use of legitimate email accounts that have been compromised through malware or social engineering to steal data or funds.
In einer krzlich durchgefhrten Studie gaben 71 der Unternehmen zu. Business email compromise scams are a sophisticated high-level cybercrime that are difficult to detect because they rely heavily on deception. Business email compromise BEC refers to all types of email attacks that do not have payloads.
It exploits the fact that so many of us rely on email to conduct businessboth personal and professional. Source link Business Email Compromise BEC bezieht sich uff aus Arten von Mail-Angriffen die keine Nutzlast nach sich ziehen. In a recent study 71 of organizations acknowledged they had seen a business email compromise.
Financial Planning. Business email compromise BEC refers to all types of email attacks that do not have payloads. Although there are numerous types there are essentially two main mechanisms through which attackers penetrate organizations utilizing BEC techniques spoofing and account take-over attacks.
Best Practices View Main Menu.

How To Tell If An Email Is Fake Or Real

Election Security Spotlight Business Email Compromise Scam

How To Protect Your Company From Email Spoofing Ironscales

Paypal Impersonated In Phishing Scam Email Claims To Offer Refund On A Recent Payment

5 Email Security Best Practices For Businesses For 2021 Dnsstuff
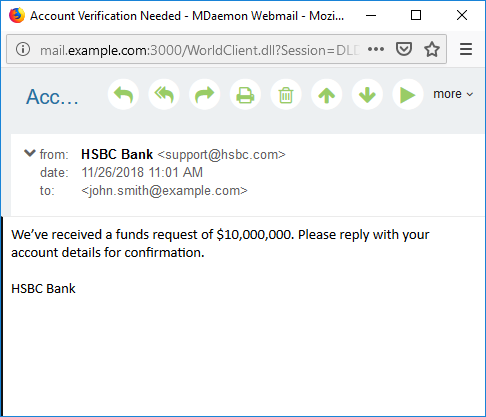
Best Practices To Avoid Business Email Compromise Ceo Fraud Attacks
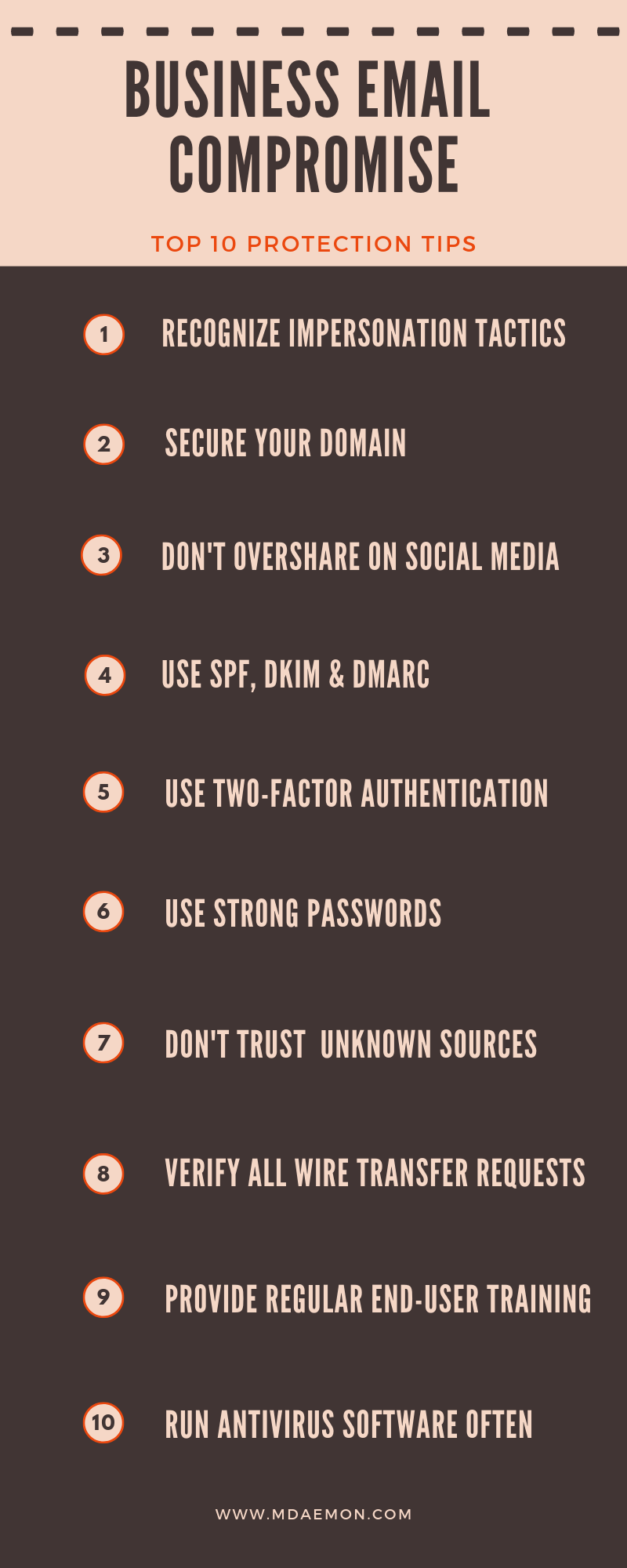
Best Practices To Avoid Business Email Compromise Ceo Fraud Attacks

How To Protect Your Company From Email Spoofing Ironscales
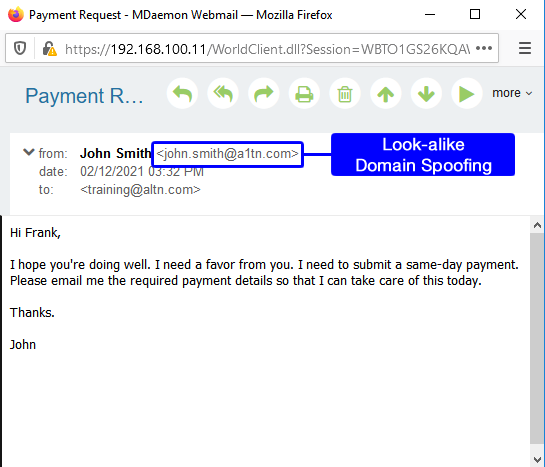
Best Practices To Avoid Business Email Compromise Ceo Fraud Attacks
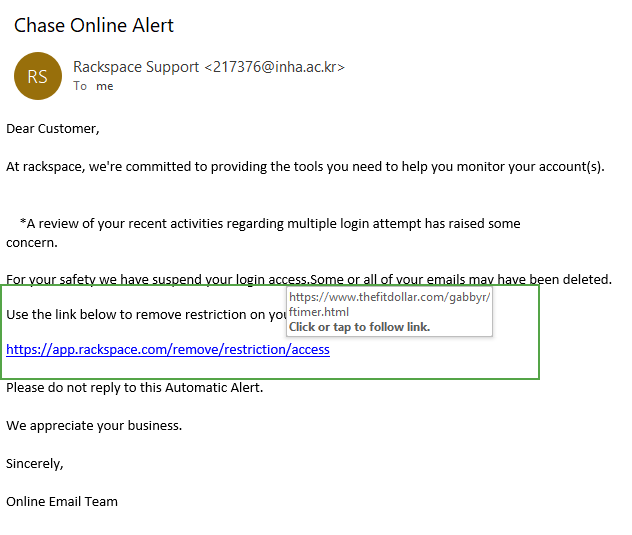
5 Common Types Of Phishing Attacks How To Recognize Avoid Them Infosec Insights
Ops Business Email Compromise Guide Fbi

Don T Be Fooled By This Audio Email Phishing Scam

5 Successful Anti Phishing Tools Ironscales

Phishing Scams Attacks How To Protect Yourself Kaspersky

How To Protect Your Company From Email Spoofing Ironscales

Best Practices To Avoid Business Email Compromise Ceo Fraud Attacks
How To Prevent Ceo Fraud Ceo Fraud Prevention Tessian
Https Www Bbt Com Content Dam Bbt Bbtcom Pdf Commercial Commercial Solutions Treasury Management Fraud Detection Mitigation Prevention Fraud Protection Update Pdf
Best Practices To Avoid Business Email Compromise Ceo Fraud Attacks
Posting Komentar untuk "Business Email Compromise Best Practices"