Business Email Compromise Attack Examples
In many cases this attack can also involve an attempt to compromise your email account through a credential phishing email. Business Email Compromise BEC is a fast-growing cybersecurity threat that all businesses especially small and medium-sized SMB ones face.

Best Practices To Avoid Business Email Compromise Ceo Fraud Attacks
Consumer privacy breaches often occur as a.

Business email compromise attack examples. Business Email Compromise BEC also referred to as a Man in the email or Man in the middle attack is a specific form of phishing where cyber criminals spoof the email addresses of an organizations executive most of the times C-level to defraud the organizations employees partners etc. These emails are an attempt to convince you to reveal critical business or financial information or process a payment request that you would never have done otherwise. This form of email attack uses impersonations to steal money from unsuspecting employees and employs conversational techniques designed to build trust between the attacker and target.
As youll recall from the examples discussed businesses have suffered staggering losses to these attacks and while users are becoming more aware of them their own human nature dictates that these threats will continue. An attacker will compromise or imitate a legitimate business account and then use this account to request fraudulent payments from customers or contacts. The premise of the attack is very simple.
In hindsight such scams sound rudimentary. Business email compromise BEC is one of the most financially damaging online crimes. A typical Business Email Compromise attack will target one or more employees.
During this type of attack the hacker may use the guise of the companys CEO or executive and send an email to a department head asking for a wire transfer funds transfer or other financial transaction. Business email compromise is a very damaging type of cyber crime in which cyber criminals impersonate the email account of an employee executive or vendor of a company for the purpose of requesting that the recipient someone from the company divulge sensitive information make payments or even share information about their companys proprietary products or technology. To make this type of attack hackers compromise corporate email accounts or create new accounts almost identical to the legitimate ones.
The FBIs Internet Crime Complaint Center IC3 reported in their 2020 Internet Crime Report that they fielded 19369 Business Email Compromise BEC complaints amounting to over 18 billion in adjusted losses in the United States for that year. Estranged relatives and Nigerian princes were ever in crisis. It exploits the fact that so many of us rely on email to conduct businessboth personal and professional.
The attacks are relatively low-tech and rely more on social engineering and trickery than. Here are five examples of BEC scams in the wild. Learn what business email compromise is BEC scams categories and how to prevent or identify these spam phishing attacks in Office 365 including mailbox rule examples and more.
This is a real-life example of a cyber-attack known as Business Email Compromise or CEO Fraud. Criminals often impersonate high-level directors or executives such as CEO and CFO. According to the 2020 FBIs Internet Crime Complaint Center IC3.
But the BEC formula used today has hardly evolved despite significant advancements in technology and attack techniques. Then attackers impersonate the owners of the email accounts and send messages to the victims. Business email compromise has come a long way since its advent in the 90s.
They needed money wired abroad -- and fast. In part one of our three-part series on Business Email Compromise BEC I explained what a BEC attack is and provided examples and statistics. Business Email Compromise falls into five primary types according to the FBI.
Business Email Compromise BEC is a cyberattack involving the hacking spoofing or impersonation of a business email address. Examples include invoice scams and spear phishing spoof attacks which are designed to gather data for other criminal activities. As attackers behind BEC attacks find ever more clever tactics to use its.
Securities and Exchange Commission revealing it was the victim of a 467 million business fraud This attack was an example of a type of BEC sometimes called Vendor Email Compromise VEC. Business email compromise BEC is a significant security threat to enterprise organizations. From there emails are then sent to employees and customers of the company in an effort to steal money and other assets.
The victim of a BEC attack receives an email that appears to come from a trusted business. In August 2015 IT company Ubiquiti filed a report to the US. Essentially its a type of targeted phishing scam with the bad guys pretending to be high-level managers legal representatives CEOs or other C-Suite execs often someone an employee feels they shouldnt challenge.
BEC is essentially an attack where the cyber attacker accesses corporate email accounts and spoofs the owners identity. The email looks and feels genuine. Business Email Compromise BEC is a type of cyber thereat or exploit which is rapidly becoming one of the most widespread email attacks faced by organizations around the world.
The Business Email Compromise BEC is a popular type of attack among cybercriminals as it targets businesses and individuals in an attempt to receive money transferred into fraudulent accounts.
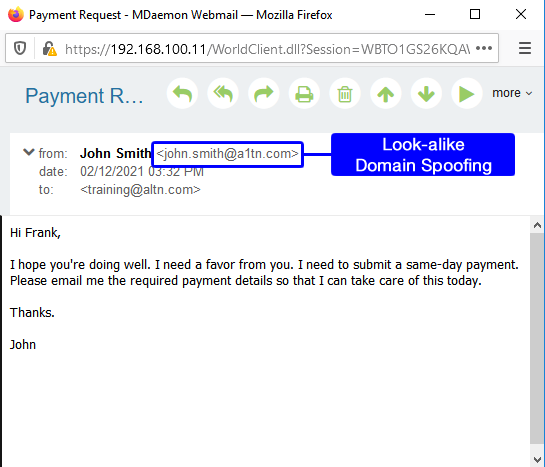
Best Practices To Avoid Business Email Compromise Ceo Fraud Attacks

Pdf Business Email Compromise Bec And Cyberpsychology
Business Email Compromise Bec Definition Prevention Gu

19 Examples Of Common Phishing Emails Terranova Security
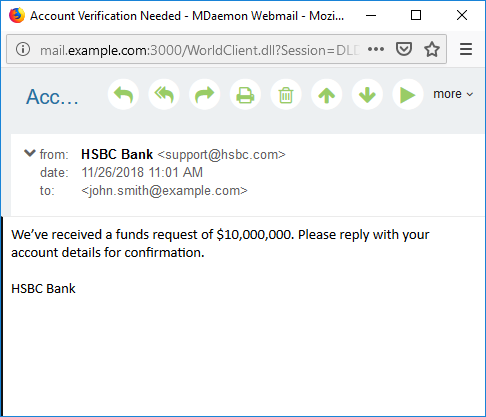
Best Practices To Avoid Business Email Compromise Ceo Fraud Attacks
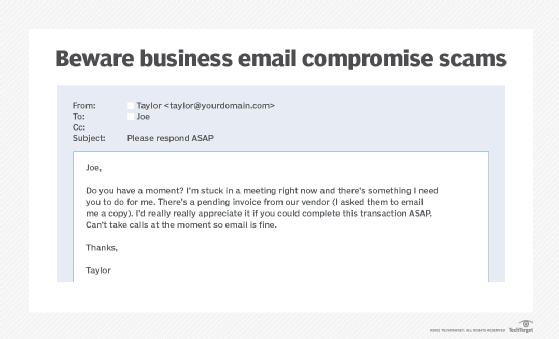
Technical Controls To Prevent Business Email Compromise Attacks
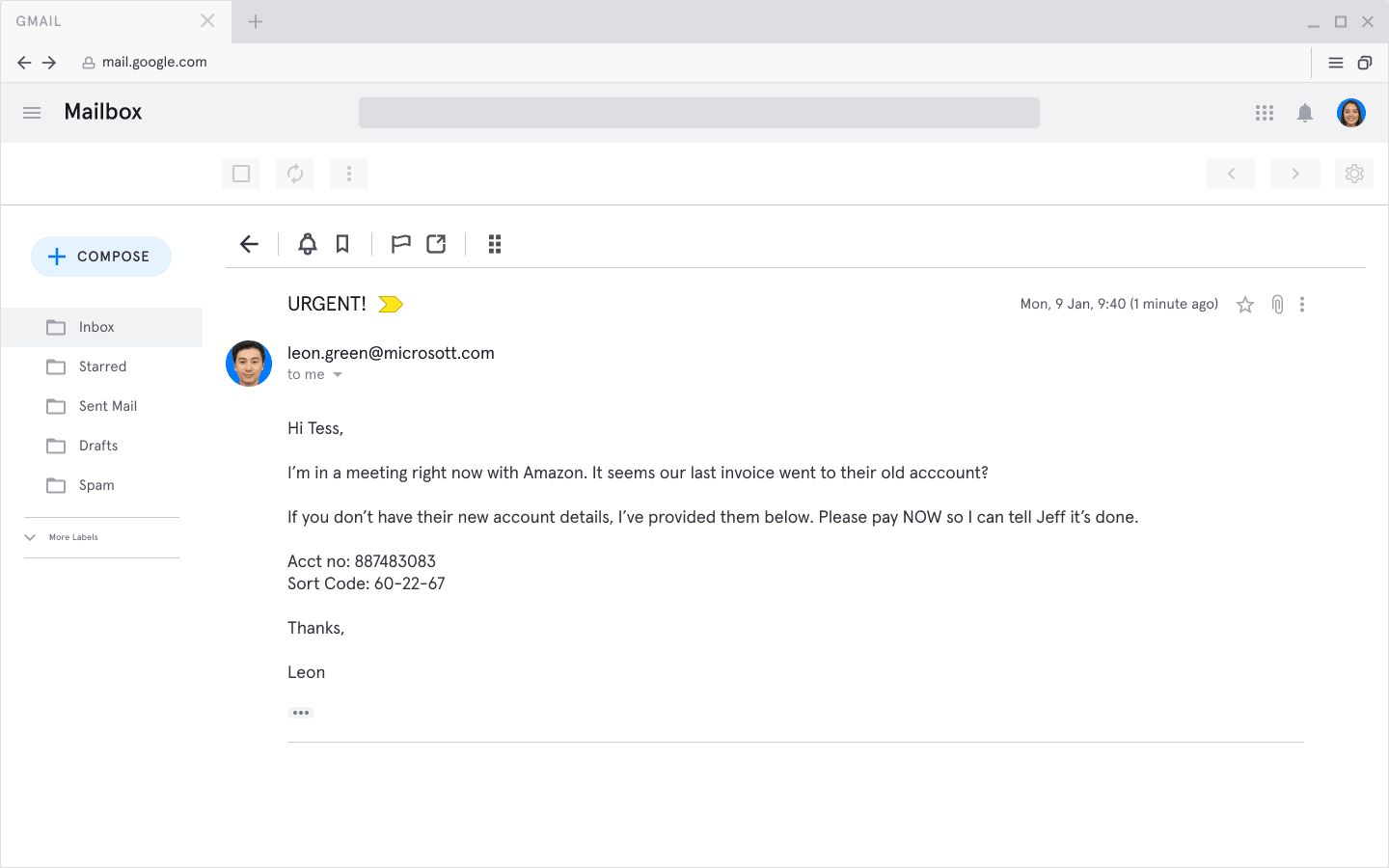
What Is Business Email Compromise Bec How Does It Work Tessian
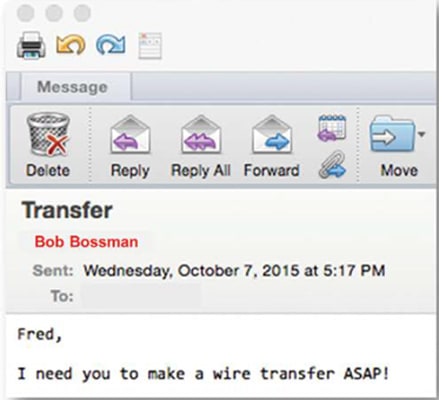
What Is Bec Business Email Compromise Meaning Proofpoint Uk
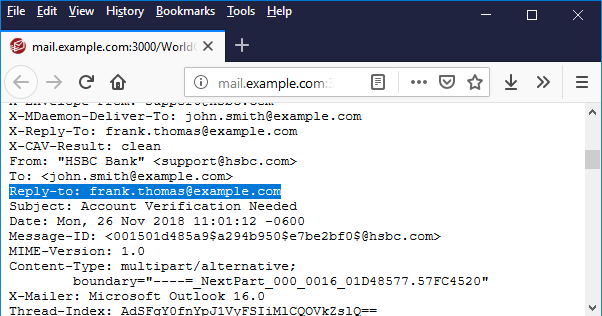
Best Practices To Avoid Business Email Compromise Ceo Fraud Attacks

Whaling Ceo Fraud Business Email Compromise Targeted Spear Phishing Attacks Continue To Trouble Business

Business Email Compromise Office 365 Making Sense Of All The Noise Youtube
Ransomware And Business Email Compromise Bec Lead Year Of Online Extortion Trendlabs Security Intelligence Blog

What Is Business Email Compromise Bec How Does It Work Tessian

Office 365 Business Email Compromise Attacks Proliferate Appriver
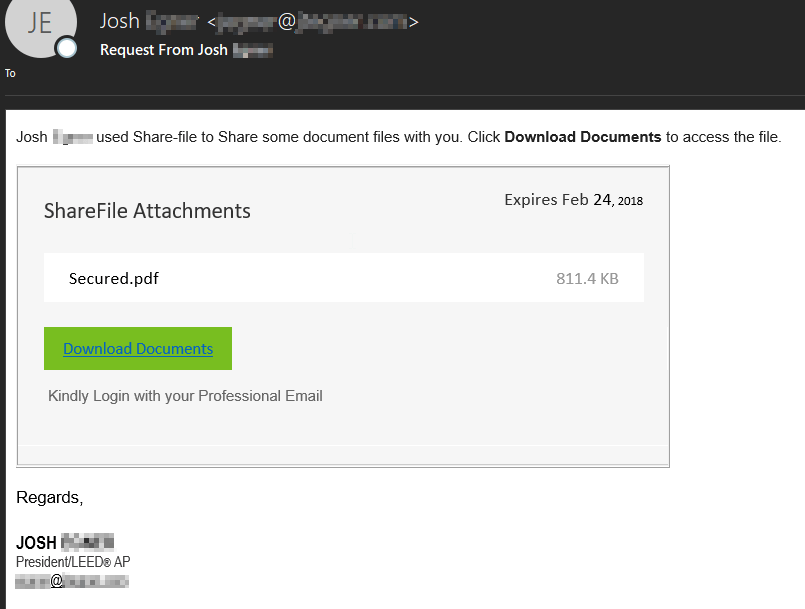
Office 365 Business Email Compromise Attacks Proliferate Appriver
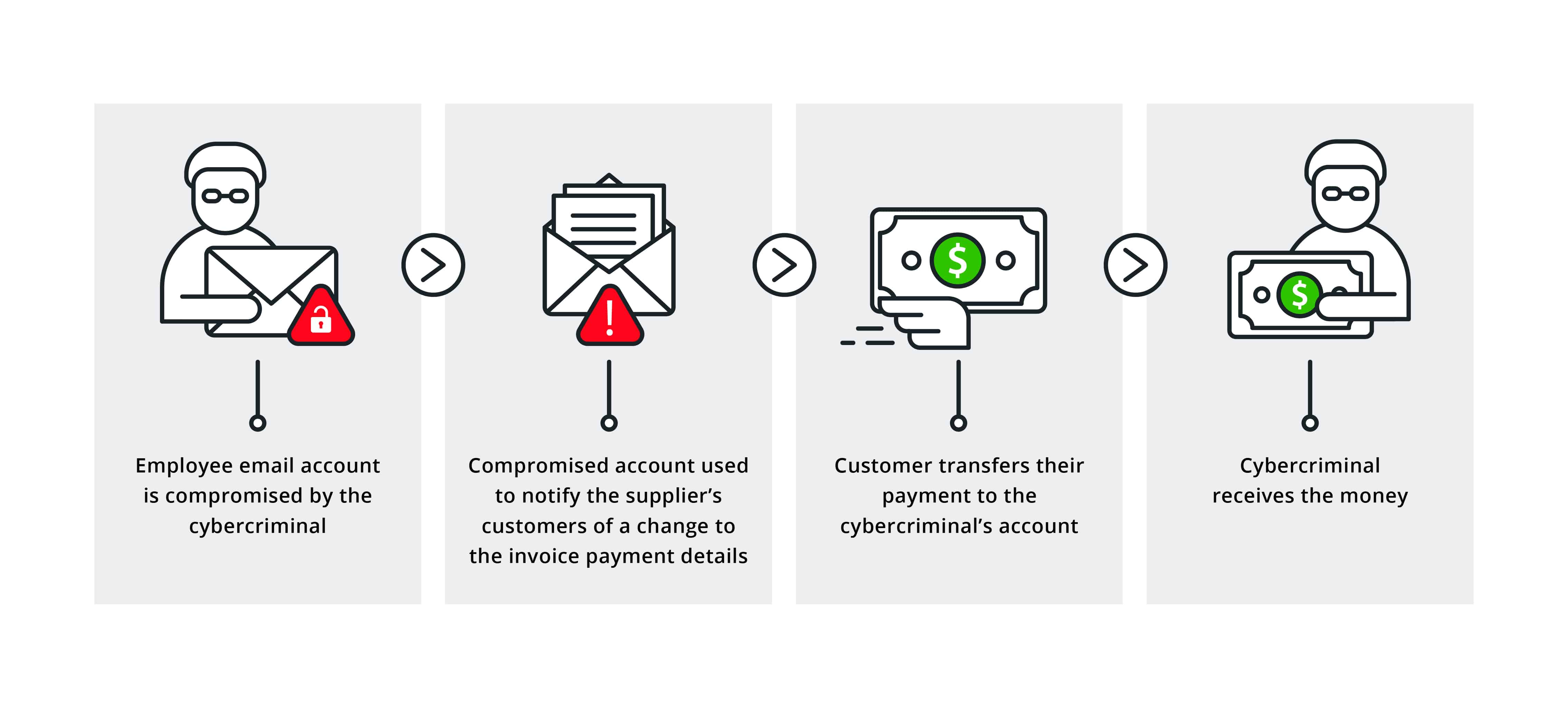
Business Email Compromise Attacks How To Protect Your Business

Business Email Compromise Attacks How To Protect Your Business

8 Real Examples Of Business Email Compromise Bec Attacks Tessian
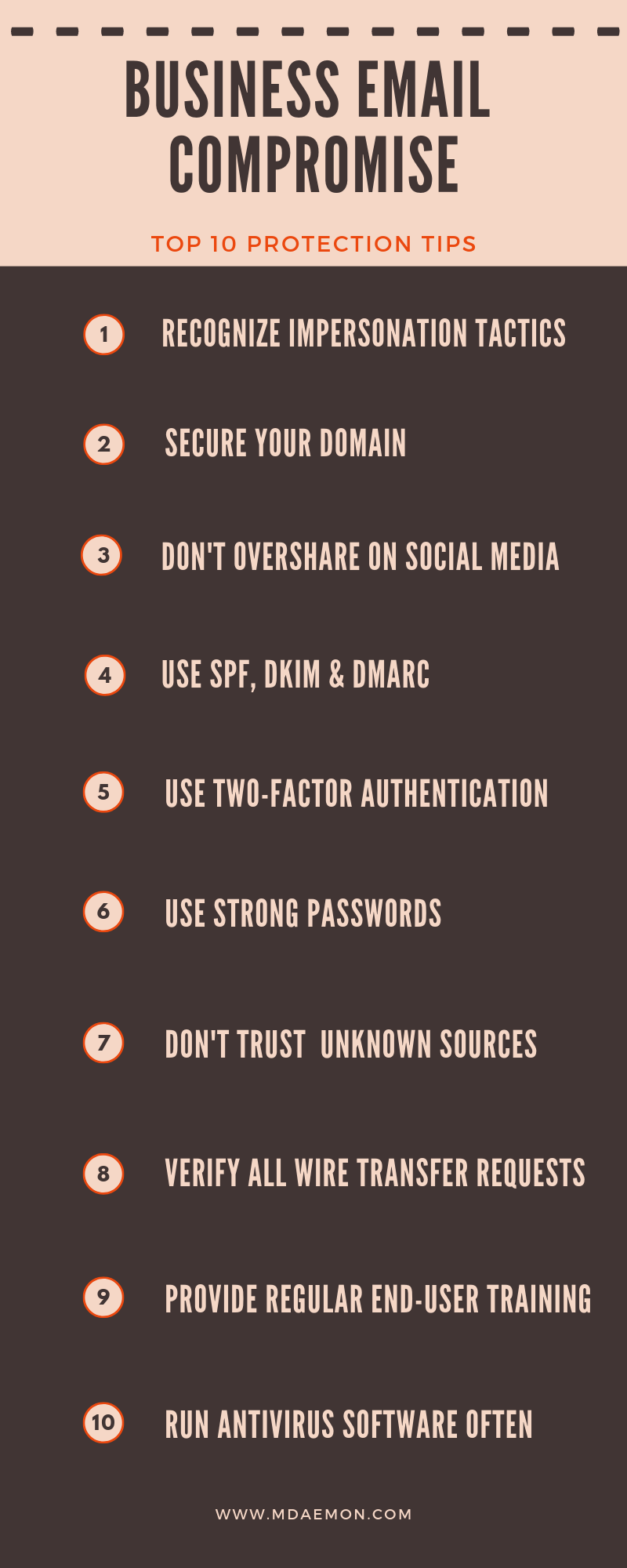
Best Practices To Avoid Business Email Compromise Ceo Fraud Attacks
Posting Komentar untuk "Business Email Compromise Attack Examples"